Current Climate
The number of cyber attacks has continued to grow in recent years. The graph below shows the number of cyber-attacks on corporate networks increasing more than 40% from 2020 to 2021. As a result, more and more people are beginning to understand the need for cybersecurity, but should Russia’s war on Ukraine cause any extra consideration to be given to the security of the United States’ cyber systems and infrastructures?
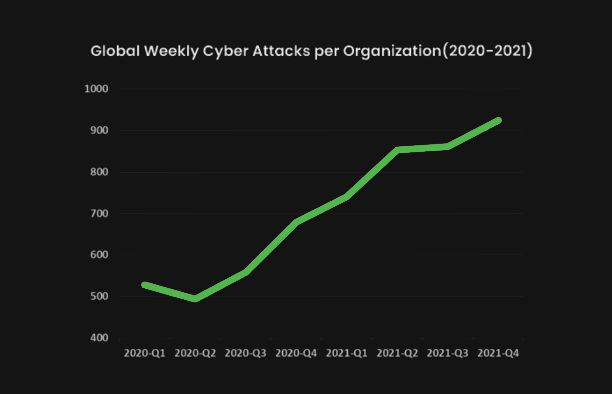
Let’s consider.
“The more Putin’s back is against the wall, the greater the severity of the tactics he may employ … one of the tools he’s most likely to use, in my view, in our view, is cyberattacks,” Biden told reporters on Monday. “The magnitude of Russia’s cyber capacity is fairly consequential, and it’s coming.”
The traditional model of criminal and nation-state attacks is changing because of the Russian war in Ukraine, Brian Contos, chief security officer of Phosphorus Cybersecurity in Nashville, Tenn., that specializes in IoT/OT and other physical systems, told TheStreet. “As both the Ukraine war and economic crisis worsens for Russia, there is a significant risk that Russia’s cyber teams will start acting out more aggressively in attacks on the U.S. and the West,” he said. The attacks would have the appearance of ransomware, “but no decryption keys will be provided if a ransom is paid,” said Sounil Yu, chief information security officer at JupiterOne, a Morrisville, North Carolina-based provider of cyber asset management and governance solutions. “The goal will be destruction, not revenue. Their goal is ruination, not remuneration,” added Yu.
Additionally, hackers from other countries like China and Iran are going to take advantage of this situation, while everyone is distracted by Russia, and will carry out their own cyber espionage operations in the U.S., Hijazi, chief executive officer of Prevailion, whose company has infiltrated numerous Russian hacking groups and monitored attempted breaches into critical U.S. infrastructure, commented.
So, to answer our question, should Russia’s war on Ukraine cause the U.S. to give extra consideration to securing our cyber systems, yes. That being the case, what can we expect to be a target?
Well, recently the United States charged four Russian government employees in major hacking efforts targeting nuclear power plants, power companies, and oil and gas firms around the world, according to indictments made public Thursday by the Department of Justice. The indictments have been under seal since mid-2021 but were made public to bolster growing concerns that Russia may unleash cyberattacks against the U.S., Europe and other nations that have opposed its ongoing invasion of Ukraine.
The energy sector is a major concern for many cyber security professionals as it is widely considered to be vulnerable and a successful attack against it could be devastatingly disruptive. There are a couple recent instances of cyber-criminal activity against energy companies. The Colonial Pipeline hack that happened just last year, in 2021, in the US is a prime example. While this attack was attributed to a group called DarkSide, there are many who still believe the Russian government played some role in the attack due to circumstantial evidence. Additionally, Russian state actors used a novel malware variant against Ukraine’s power grid in 2016, causing widespread blackouts across the country.
How and why is the energy sector vulnerable?
Power generation and transmission or distribution systems are run by industrial control systems that are largely built on computer systems and software. This change has also created vulnerabilities due to the interconnected nature of these systems. Hackers could simply knock out the front-office networks to disrupt operations without harming the industrial controls systems. Another option is to attack the control systems directly, causing physical machinery to malfunction or damage, and resulting in long-term and costly disruptions in the energy supply, from electric grid blackouts to disruptions in the supply of oil and gas. They could also go after the shipping industry from the ports to the shipping freighters themselves or the communications/navigations systems they rely on to disrupt LNG shipments.
Things that may be targeted will be controllers of power regulation like circuit breakers and substations. Those are the computers that control the flow of energy, Josh Rickard, security solutions architect at Swimlane, a Boulder, Colo.-based provider of low-code security automation, told TheStreet. Hackers could either slowly or immediately disable portions of the power or choose to disconnect from the power grid entirely.
What other targets could there be?
Nearly a month into Russia’s invasion of Ukraine, the FBI conducted a court-authorized operation in March 2022, disrupting a two-tiered global botnet of thousands of infected network hardware devices under the control of a threat actor known as Sandworm, which the U.S. government previously attributed to the Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation (the GRU), the Justice Department announced in a statement.
The operation copied and removed malware from firewall devices that Sandworm used for command-and-control of the botnet (a network of hacked computers that can bombard other servers with rogue traffic). While the operation did not access the Sandworm malware on the underlying victim devices, the disabling of the command-and-control mechanism severed the bots from the Sandworm devices’ control, disrupting the Russian military hacker operation.
“Through close collaboration with WatchGuard [Technologies Inc.] and our law enforcement partners, we identified, disrupted and exposed yet another example of the Russian GRU’s hacking of innocent victims in the United States and around the world,” U.S. Attorney Cindy K. Chung for the Western District of Pennsylvania said in a statement. “Such activities are not only criminal but also threaten the national security of the United States and its allies,” Chung added.
While the FBI operation succeeded in copying and removing the malware from all remaining identified command-and-control devices and prevented Sandworm from accessing these devices, WatchGuard and ASUS devices that acted as bots may remain vulnerable to Sandworm if device owners do not take the WatchGuard and ASUS recommended detection and remediation steps, DOJ warned. The department urged network defenders and device owners to review the department’s Feb. 23 advisory and the guidance documents that WatchGuard and ASUS released.
Sailors and other military officials were warned in February they were targets for cyberattacks amid troubled Sino-U.S. relations and Russia’s invasion of Ukraine.
“Cyberattacks against businesses and U.S. infrastructure are increasing in frequency and complexity,” Navy Vice Adm. Jeffrey Trussler said in an unclassified memo at the time. “[Department of Defense] and federal law enforcement report adversary interest in our remote work infrastructure. This means that you are a target — for your access and your information.”
Hackers previously exploited mistakes on Navy and private networks by stealing or brute-forcing credentials as well as surreptitiously installing malware, according to the memo. Defense News in June 2018 reported Chinese-sponsored cyberattacks breached a Navy contractor’s computers, jeopardizing sensitive data related to secret work on an anti-ship missile.
I think the following two quotes, one from Navy Vice Adm. Jeffrey Trussler and one from Deputy Attorney General Lisa Monaco, best summarize how we should be considering U.S. cyber security in the wake of Russia’s war on Ukraine.
Deputy Attorney General Lisa Monaco said in a statement following the public release of four indictments of Russian government employees by the Department of Justice: “Russian state-sponsored hackers pose a serious and persistent threat to critical infrastructure both in the United States and around the world. Although the criminal charges unsealed today reflect past activity, they make crystal clear the urgent ongoing need for American businesses to harden their defenses and remain vigilant.”
Navy Vice Adm. Jeffrey Trussler said in his February missive to sailors and other military officials, “With heightened tensions throughout the world, ensure your team understands how the actions of a single user can impact our global force.”